Security Management Reimagined
MeldSecurity unifies vulnerability intelligence, threat detection, and security operations into one powerful platform trusted by security teams worldwide.
Stay Ahead of Vulnerabilities with Real-Time Intelligence
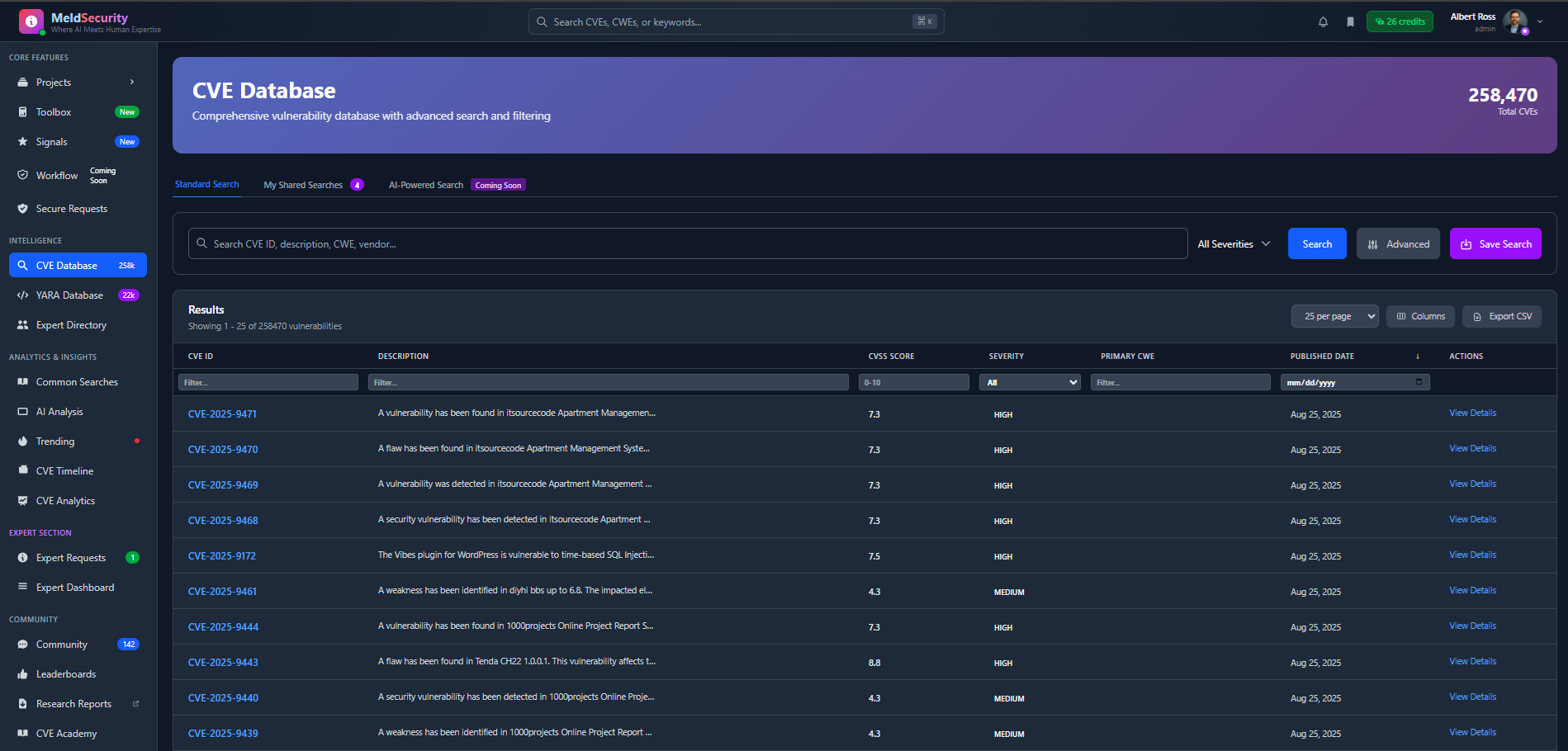
Access the industry's most comprehensive vulnerability database with over 258,470 CVEs, updated in real-time from NIST NVD and enriched with expert analysis.
-
Advanced Search & FilteringFind vulnerabilities instantly with severity filters, CWE mapping, and smart search across 25 years of data
-
AI-Powered InsightsGet instant analysis with using local or bring-your-own-model AI integration for vulnerability impact assessment
-
Shared SearchesSave and share complex search queries with your team for consistent monitoring
Transform Raw CVE Data into Actionable Security Intelligence
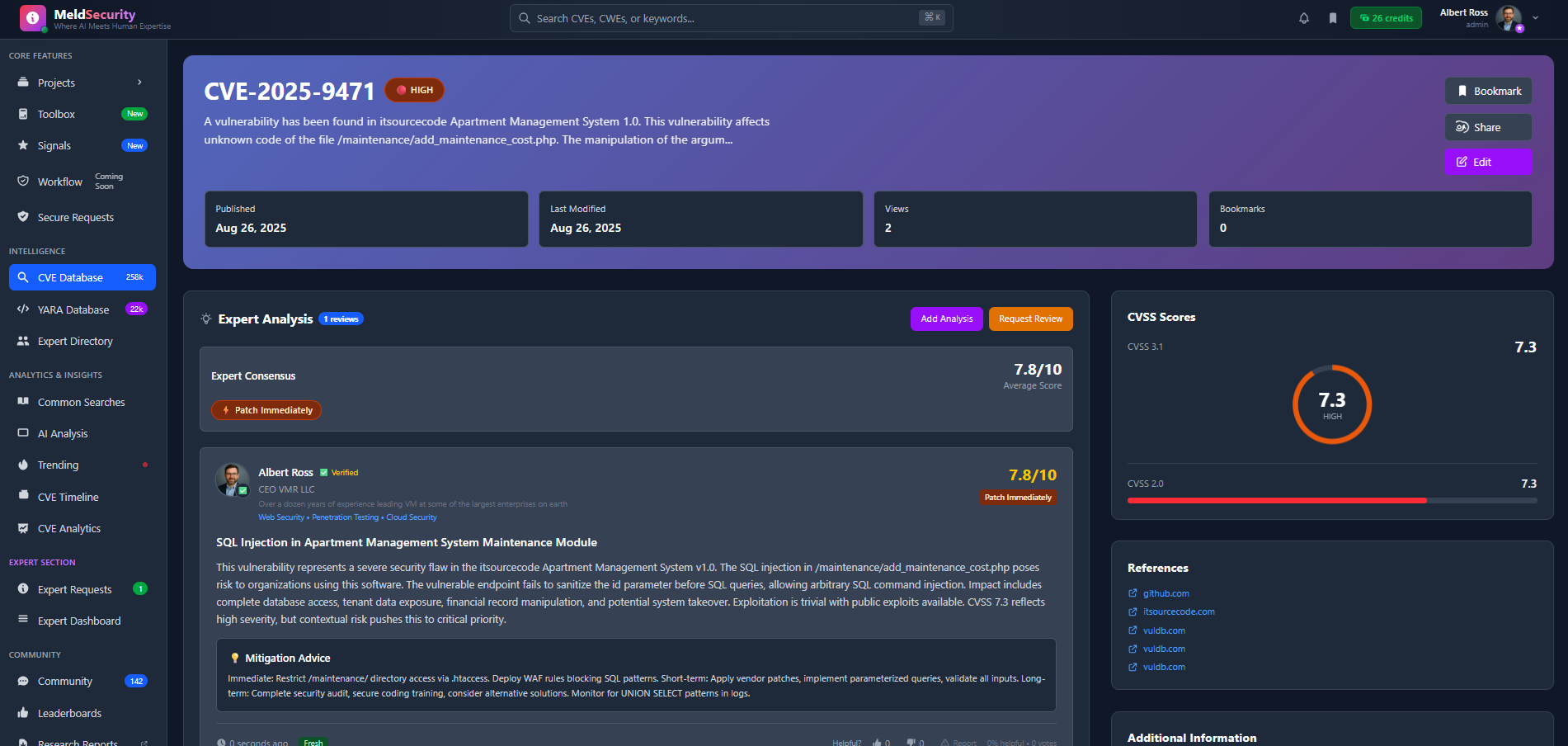
Go beyond basic vulnerability data with expert analysis, CVSS scoring breakdowns, and contextual threat assessments from verified security professionals.
-
Detailed CVSS AnalysisVisual breakdowns of CVSS v3.1 and v2.0 scores with impact metrics
-
Expert Review SystemSubmit vulnerabilities for expert analysis and get professional recommendations
-
Reference AggregationAccess curated links to patches, advisories, and exploit databases
Organize Security Operations with Intelligent Project Workflows
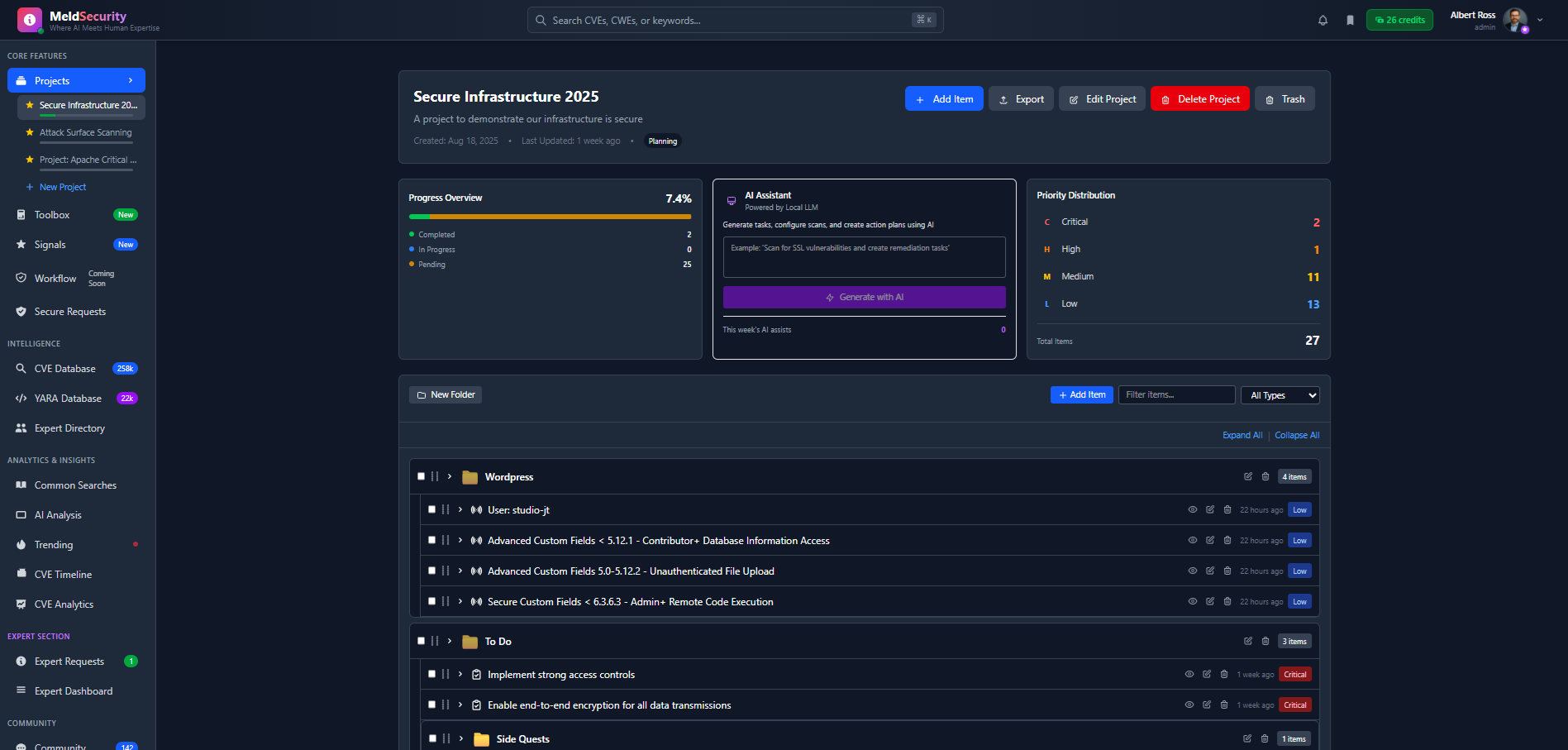
Transform chaotic security data into organized, actionable projects. Track vulnerabilities, manage remediation efforts, and maintain security posture across your entire infrastructure.
-
Smart Folder OrganizationHierarchical folder structure with drag-and-drop management for security items
-
Priority-Based TrackingVisual indicators for critical, high, medium, and low priority security issues
-
AI-Powered AssistantGenerate remediation plans and security recommendations with integrated AI
Discover Vulnerabilities Before Attackers Do
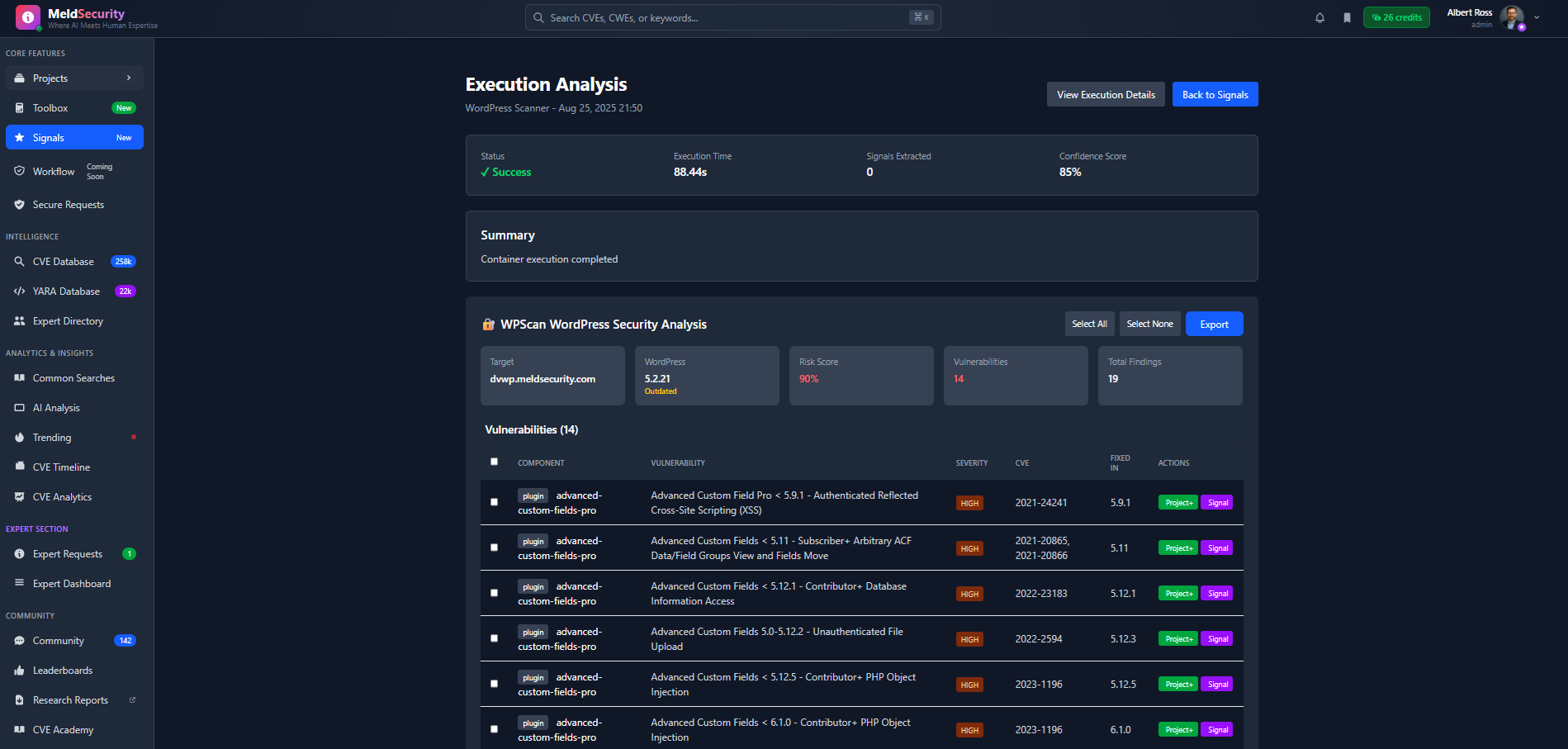
Deploy enterprise-grade security scanning across your entire digital infrastructure. From CMS platforms and web applications to APIs, containers, and cloud environments - identify and remediate vulnerabilities before they become breaches.
-
Multi-Platform CMS & Framework DetectionWordPress, Joomla, Drupal, Magento, Laravel, Django, Ruby on Rails, and 50+ other platforms with plugin/module vulnerability scanning
-
Infrastructure & Network ScanningPort scanning, service enumeration, SSL/TLS analysis, subdomain discovery, DNS reconnaissance, and cloud configuration auditing (AWS, Azure, GCP)
-
Advanced Web Application TestingSQL injection, XSS, CSRF, XXE, SSRF, path traversal, authentication bypass, session hijacking, and OWASP Top 10 vulnerability detection
-
API Security TestingREST/GraphQL/SOAP API scanning, authentication testing, rate limiting checks, data exposure analysis, and API versioning vulnerabilities
-
Container & Kubernetes SecurityDocker image scanning, Kubernetes misconfigurations, container escape detection, secrets exposure, and supply chain vulnerability analysis
-
Source Code & Dependency AnalysisSAST scanning, open source license compliance, outdated dependency detection, secrets scanning in code repositories, and supply chain risk assessment
-
Compliance & Configuration AuditingPCI DSS, HIPAA, GDPR compliance checks, CIS benchmarks, security headers analysis, and infrastructure-as-code security validation
-
AI-Powered Risk Scoring & PrioritizationMachine learning-based vulnerability correlation, contextual risk scoring, exploit prediction, and automated remediation recommendations with confidence metrics
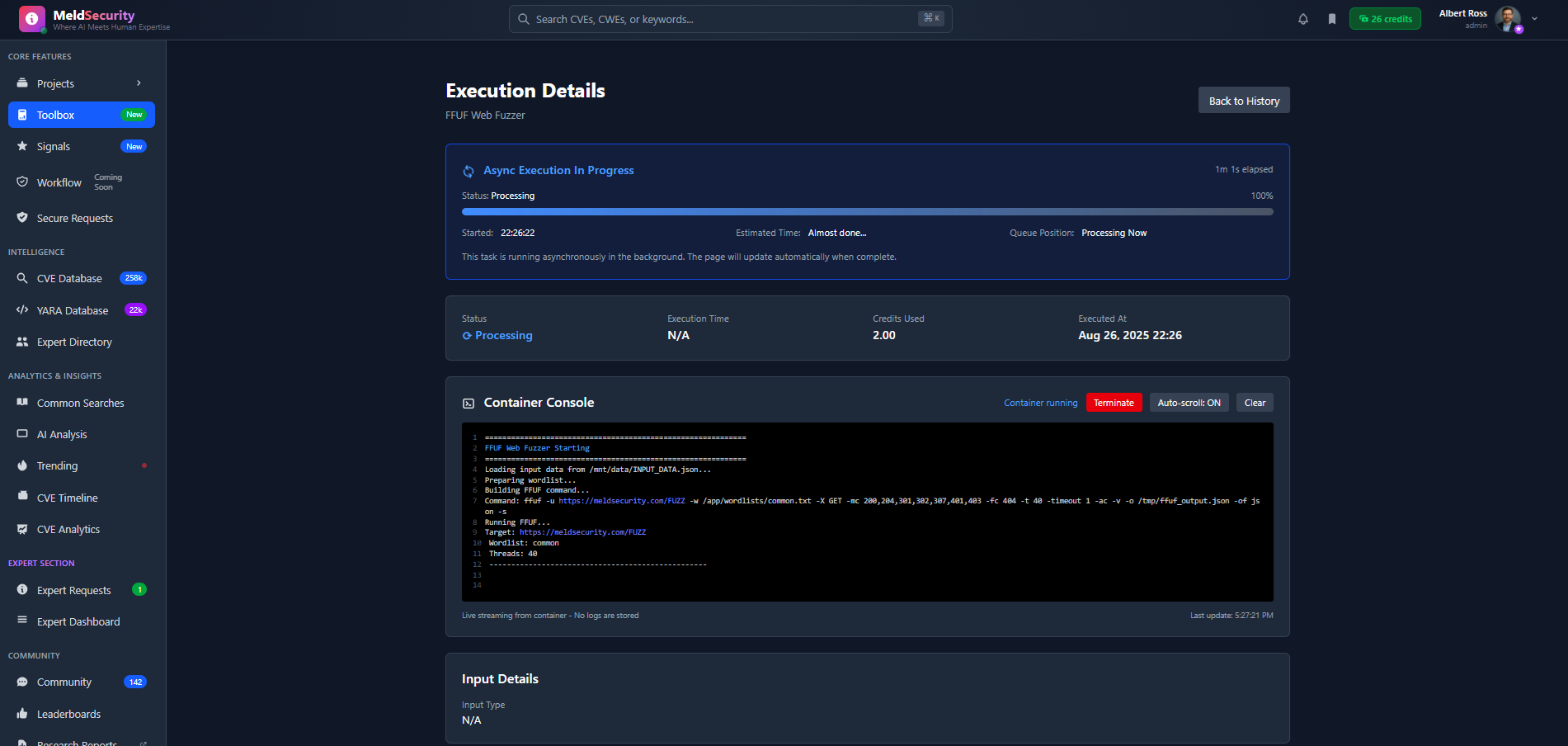
Execute Security Tools at Enterprise Scale
Run security tools and vulnerability scanners in completely isolated containerized environments.
-
Fully Isolated Container ExecutionEach security scan runs in its own ephemeral sandboxed container with dedicated resources and network isolation
-
Real-Time Streaming ConsoleLive execution monitoring with WebSocket-based terminal output, progress tracking, and instant alerts for critical findings
-
Transparent Usage-Based PricingPay only for compute resources used with detailed breakdowns, credit-based allocation, and no hidden infrastructure costs
-
Multi-Cloud InfrastructureDistributed across multiple cloud providers and regions for maximum reliability, performance, and compliance with data residency requirements
-
Dynamic Resource AllocationAutomatic scaling from lightweight scans to heavy fuzzing operations with GPU acceleration for cryptographic analysis when needed
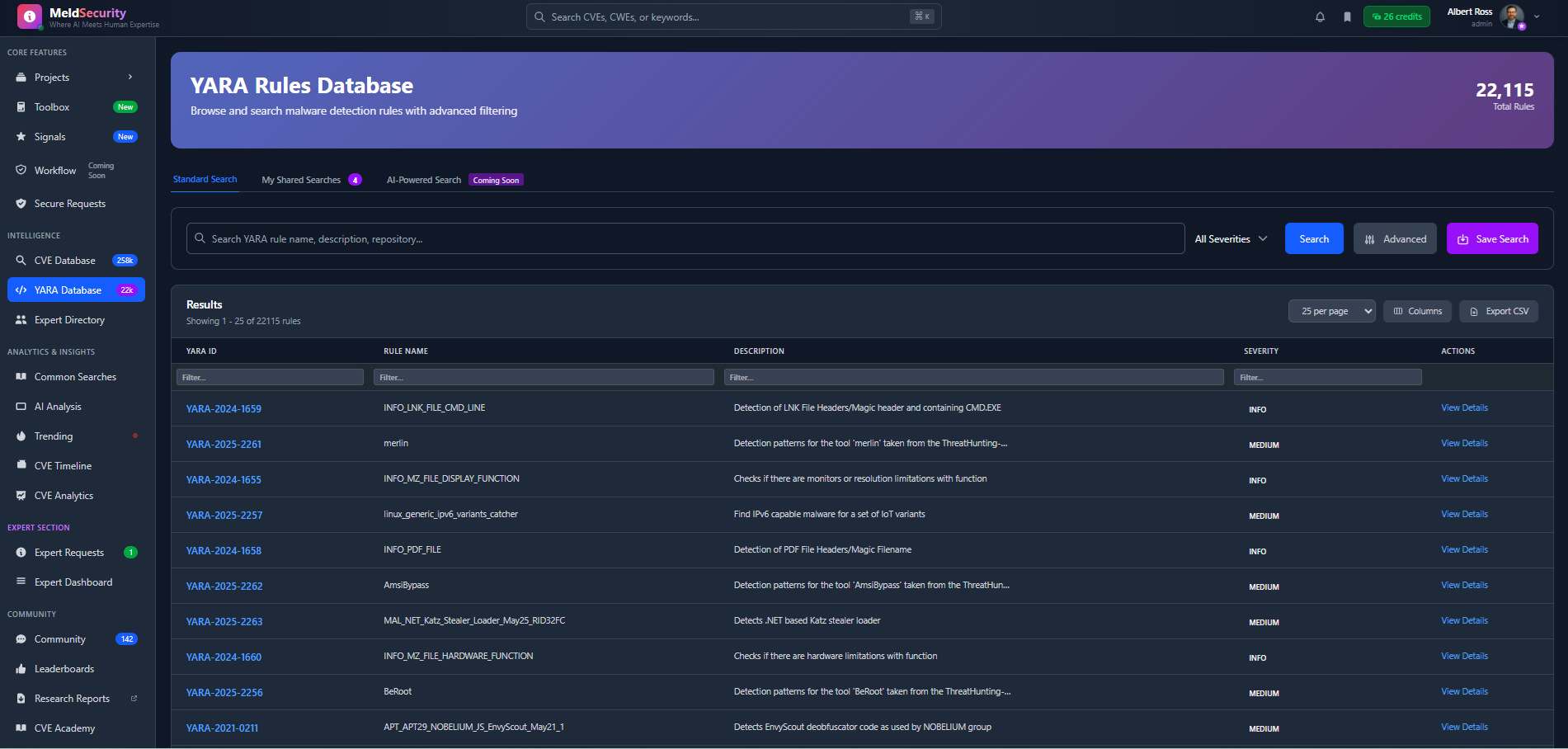
Hunt Malware with 22,000+ Battle-Tested YARA Rules
Access one of the industry's most comprehensive YARA rule database for malware detection, threat hunting, and incident response with real-time updates and community contributions.
-
Comprehensive Rule Library22,115+ curated YARA rules covering malware families, APT groups, and IoT threats
-
Advanced SearchFind rules by malware type, severity, or threat actor with intelligent filtering
-
Export & IntegrationDownload rules for use in your security tools or integrate via API
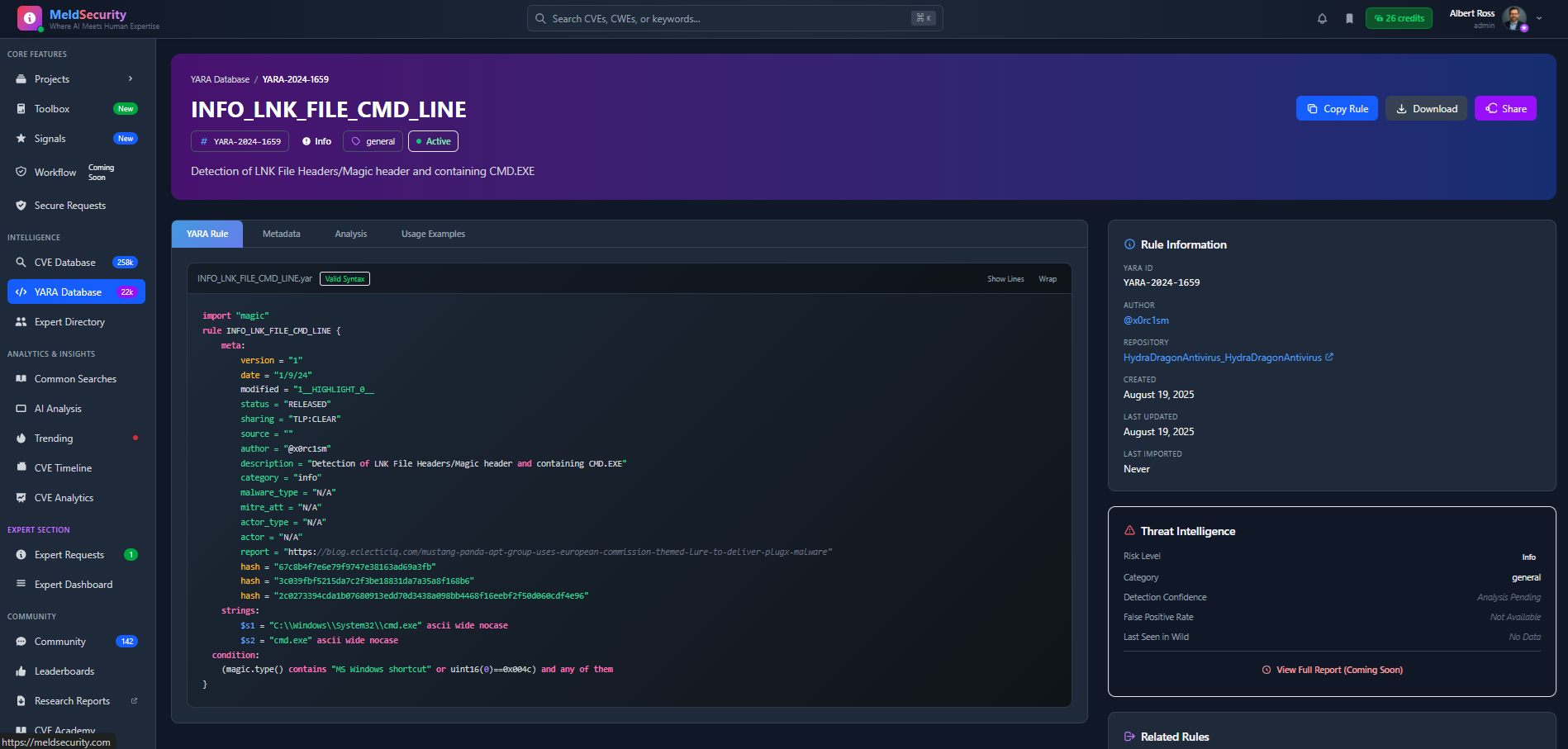
Deep-Dive into Malware Patterns with Syntax-Highlighted Rules
Understand malware detection patterns with detailed rule analysis, syntax highlighting, and contextual threat intelligence for effective threat hunting.
-
Syntax-Highlighted CodeColor-coded YARA rule syntax for easy understanding and analysis
-
Rule MetadataAuthor information, creation dates, and threat intelligence context
-
Related RulesDiscover similar patterns and related threat detection rules
Ready to Transform Your Security Operations?
Join thousands of security professionals who trust MeldSecurity to protect their infrastructure.
No credit card required • Full access to all features • Cancel anytime
